Algorithmic Siege Warfare: How Coordinated Anti-Israel Networks "Break the System"
JISS and JCFA research reveals how pro-Palestinian networks exploit social media and generational vulnerabilities to achieve diplomatic victories that traditional statecraft cannot easily counter
Two recent analyses from Israeli research institutions highlight a salient aspect of digital warfare where social media algorithms become weapons to reshape global opinion and achieve geopolitical objectives without traditional diplomacy.
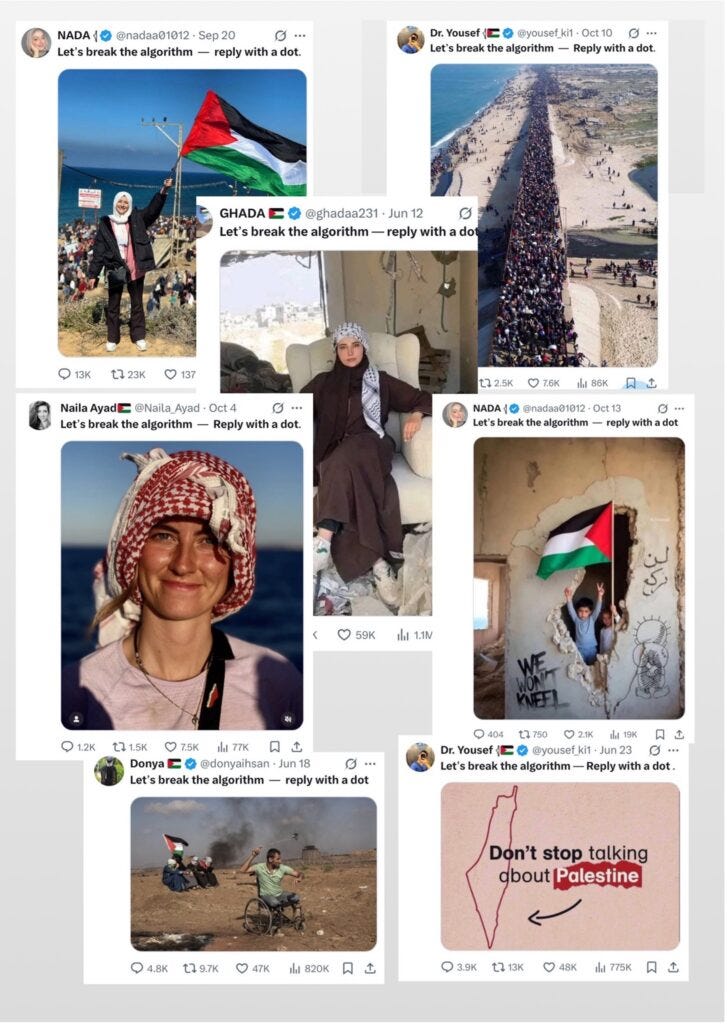
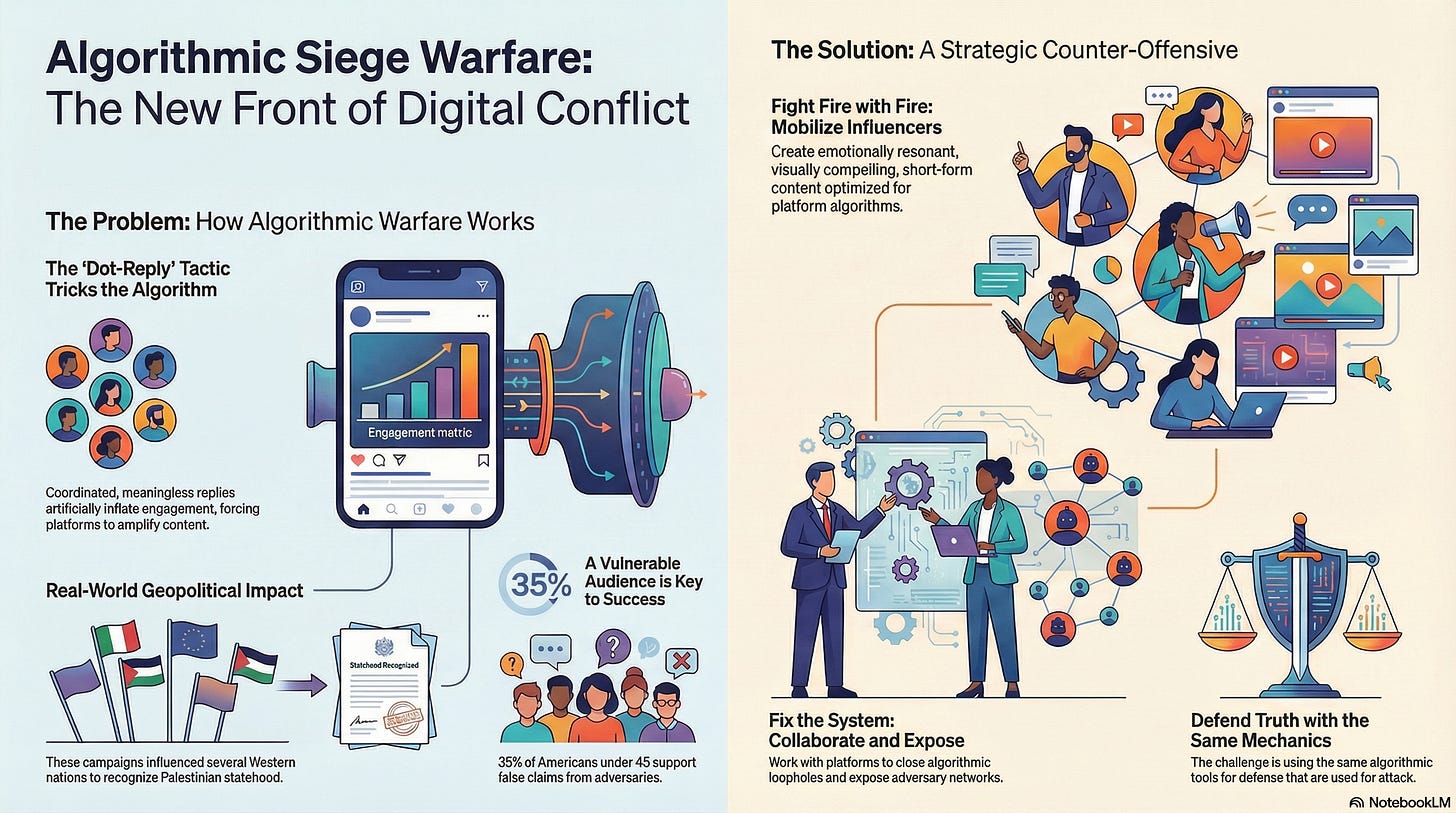
The Jerusalem Institute for Strategy and Security (JISS) has identified “Algorithmic Siege Warfare”—a tactical evolution centered on a deceptively simple technique. Coordinated networks instruct supporters to “break the algorithm – reply with a dot.” These semantically meaningless replies artificially inflate engagement metrics, triggering platform algorithms to amplify content to wider audiences.
Each dot functions as a signal to platforms like X (formerly Twitter) that a post is popular, forcing preferential visibility for emotionally charged content depicting civilian casualties and destruction. According to JISS researchers, this represents a fundamental shift from persuasion to system manipulation, operating on two levels: computational manipulation through high-volume replies that exploit platform architecture, and affective engineering through strategically curated imagery designed to trigger emotional responses that algorithms privilege.
The geopolitical impact has been tangible. JISS suggests these campaigns contributed to the recognition of Palestinian statehood by several EU member states, Canada, Australia, and the United Kingdom—demonstrating how non-state actors achieve strategic objectives through algorithmic manipulation.
Why It Works: The Vulnerable Audience
The real-world impact of these tactics is measurable. According to the 2025 Nation Brands Index, Israel ranks last among 50 countries surveyed, with the steepest decline among 18-24 year-olds. A new analysis from the Jerusalem Center for Security and Foreign Affairs (JCFA) explains this generational vulnerability. Younger audiences consume information through platforms that favor rapid emotional engagement over depth, making them particularly susceptible to the algorithmic manipulation tactics JISS documented.
JCFA surveys reveal up to 35% of Americans under 45 support Hamas’s false claims even when explicitly told the source. Social media has transformed how knowledge circulates—complex historical narratives compress into emotionally charged memes optimized for viral sharing, while nuanced context struggles to gain traction.
The manipulation extends beyond grassroots campaigns. Both analyses document coordinated state-level information warfare: Iran creates fake news websites and deploys bot networks; Russia and China amplify anti-Israel content through state media; Qatar’s Al Jazeera serves as a major platform for anti-Israel messaging.
Strategic Response: Fighting Back in the Digital Arena
Both institutions agree traditional public diplomacy has failed because it was designed for a different media environment. Their recommendations focus on tactical adaptation:
Immediate Actions:
Mobilize influencers who understand platform mechanics and create emotionally resonant, visually compelling content
Build rapid response capabilities to counter viral misinformation before narratives solidify
Produce short-form educational content optimized for platform algorithms
Structural Changes:
Collaborate with social media platforms to fix algorithmic vulnerabilities that enable coordinated manipulation
Expose adversaries’ information warfare operations and coordination networks
Provide training and resources for pro-Israel content creators to compete in the attention economy
Together, these analyses expose a systemic vulnerability in how democratic societies process information—one that any adversary with smartphones and coordination can exploit. The challenge isn’t whether we approve of this transformation, but whether we’re prepared to defend truth using the same algorithmic mechanics that weaponize it.




Wow. Great report. What does it take to get this implemented?
A reverse gear would have been needed